Zero Trust UAS Group – ZTUG Introductory Paper
Overview
The Zero Trust UAS Group (ZTUG) is a U.S. government research consortium focused on securing Unmanned Aircraft Systems (UAS) for mission-critical federal use, including the Department of Defense (DoD), Department of Homeland Security (DHS), and coalition partners. Their goal is to ensure UAS are secure, resilient, and interoperable, aligned with U.S. government zero trust and aviation standards.
The proposed architecture builds on:
NIST Zero Trust Architecture
DoD Zero Trust Reference Architecture
DHS/CISA UAS guidance
NASA & FAA UAS Traffic Management (UTM) requirements
FY-2026 U.S. federal UAS investment priorities (~$3B earmarked for UAS and counter-UAS)
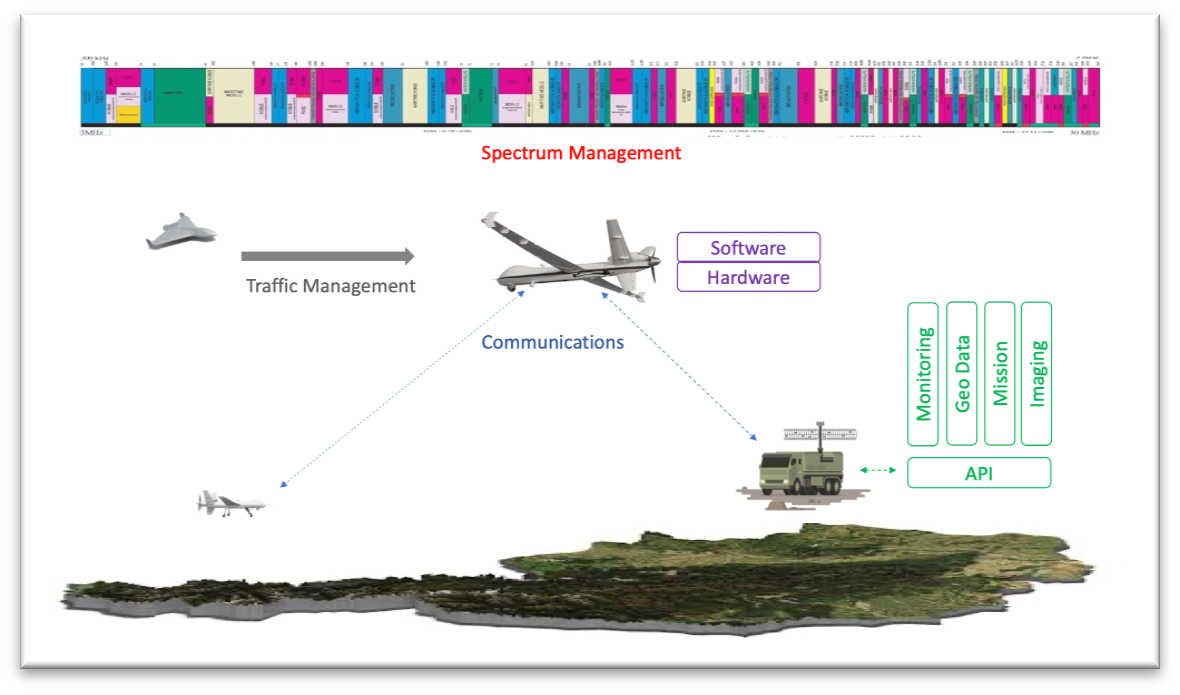
Five ZTUG Focus Areas
1. Hardware and Software Integrity
Risks: Supply chain infiltration (counterfeit/malicious parts), firmware backdoors, debug port exploitation, EMP/overheating attacks.
Solutions:
Hardware root of trust (TPMs, HSMs)
Secure boot & verified firmware
SBOMs (Software/Hardware Bill of Materials) for lifecycle tracking
Anti-tamper per NIST SP 800-53 SA-10(3)
Testing per MIL-STD-883
Supply chain vetting via DoD’s Blue UAS framework
2. Secure Communication
Risks: Man-in-the-middle attacks, GPS spoofing, key recovery via side channels, denial-of-service.
Solutions:
FIPS 140-3 validated crypto modules
Digital signatures & integrity checks for command links
GPS anti-spoofing with inertial backups
Migration toward Post-Quantum Cryptography (PQC)
3. Spectrum Management
Risks: Jamming, unauthorized signal injection, congestion in urban/battlefield environments.
Solutions:
Dynamic spectrum allocation & channel scanning
Multi-band redundancy (SATCOM, 5G, unlicensed bands)
Continuous spectrum monitoring with automated evasive maneuvers
FAA Beyond Visual Line of Sight (BVLOS) compliance
4. Secure API Support
Risks: Credential theft, malicious payload injection, over-permissioned APIs enabling lateral attacks.
Solutions:
Zero Trust authentication/authorization (OAuth2 + least privilege)
NIST Secure Software Development Framework (SSDF) for lifecycle security
Real-time API anomaly detection
Compliance with FISMA, NIST SP 800-53, and FIPS 200
5. Traffic Management
Risks: Remote ID spoofing/replay, USS (UAS Service Supplier) disruption via data poisoning or DoS, unsafe flight planning.
Solutions:
Cryptographically authenticated Remote ID with redundancy
Zero Trust segmentation of UTM cloud services
Strong API controls for UTM providers
Compliance with FAA Remote ID Rule (2021), FAA UTM NPRM (2025), and ASTM F38 standards
Key Recommendations
ZTUG advises DoD, DHS, and federal agencies to:
Implement Zero Trust Data & Network security from hardware roots of trust to API governance.
Require hardware/software integrity controls with FIPS-validated crypto and MIL-STD-883 testing.
Secure all UAS communications with PQC-ready encryption.
Build spectrum resilience and FAA/NASA UTM compliance into operations.
Enforce UTM & Remote ID compliance for interoperability and airspace safety.
Implications
Strategic Alignment: Supports the FY-2026 UAS funding wave (~$3B) and national security priorities.
Interoperability: Ensures UAS can safely operate across agencies and with allies.
Resilience & Safety: Reduces mission risk, protects sensitive data, and strengthens compliance with both aviation safety and cybersecurity mandates.
This document establishes ZTUG’s Zero Trust UAS Architecture as a baseline security and resilience model for federal UAS adoption, integrating Zero Trust principles with aviation regulatory requirements.