Zero Trust AI-Managed PQC (ZAP): The Future of Secure Mobility
As Unmanned Aircraft Systems (UAS), Autonomous Vehicles (AV), and satellite networks become more intelligent and connected, they also become prime targets for next-generation cyber threats. Traditional perimeter-based defenses cannot protect these systems from quantum-capable adversaries who can intercept and decrypt wireless communications. The newly published Zero Trust AI PQC report from the Zero Trust UAS Group (ZTUG) introduces a breakthrough framework—Zero Trust AI-Managed Post-Quantum Cryptography (ZAP)—to secure advanced mobility systems at the data layer.
The Problem: Mobile Systems Are Exposed
Modern mobile and space systems rely on wireless communications that are easy to detect and monitor. Quantum computing advances threaten current encryption methods, enabling attackers to decrypt transmissions, recover private keys, and inject malicious data into mission-critical networks. While Post-Quantum Cryptography (PQC) promises protection against these future threats, it introduces new challenges: computational load, key size, latency, and complex configuration—especially in constrained edge environments like drones or satellite terminals.
The Solution: AI + Zero Trust + PQC
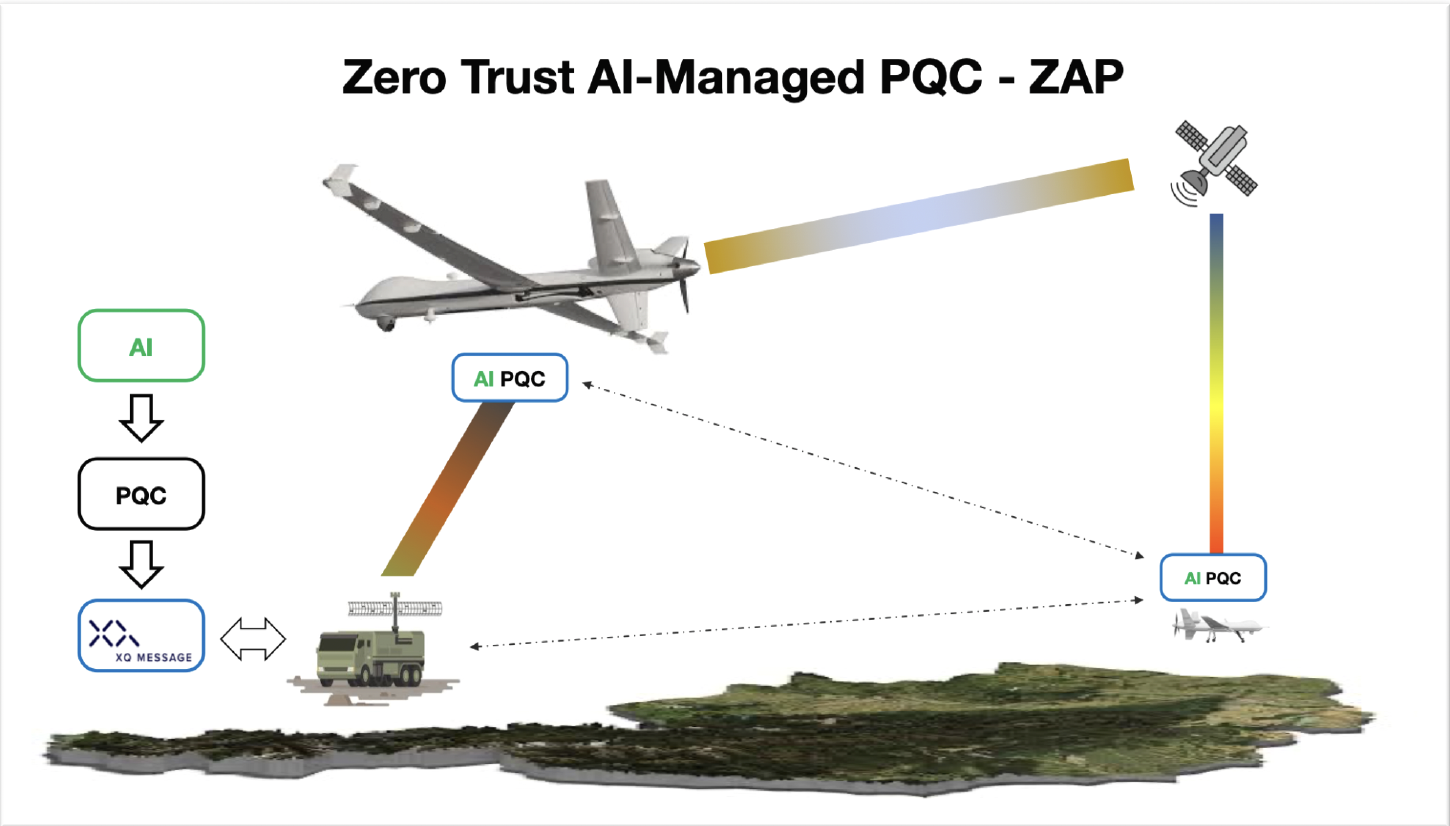
The ZAP model integrates Zero Trust Data Security, AI-driven configuration, and Post-Quantum Cryptography into a unified architecture that verifies every node, every key, and every packet. Here’s how it works:
Zero Trust Data Foundation
Each data object is encrypted with a unique key, enforcing object-level security. Keys are stored separately from the data, and only verified nodes can request access through PQC-secured exchanges like CRYSTALS-Kyber and Dilithium.AI-Managed PQC Configuration
An edge AI agent continuously evaluates CPU load, link quality, and mission constraints to select the optimal PQC algorithm and parameters—automating what was once a complex manual process. This enables real-time adaptation to changes in bandwidth, latency, or RF conditions.Quantum-Resilient Access Control
Policies differentiate between fixed and mobile endpoints. Drones or vehicles use short-lived, PQC-protected keys with location- and posture-based access control. Every key event—generation, rotation, or revocation—is logged and signed using PQC digital signatures to ensure non-repudiation.Timing Attack Defense
AI agents detect microarchitectural and timing-based side-channel attacks—an emerging threat to wireless PQC systems—and adjust configurations dynamically to minimize leakage.
XQ Message: Real-World Implementation
The ZAP model leverages the XQ Message Zero Trust Data Platform as a commercial implementation of these principles. XQ’s policy server manages PQC digital certificates, enforces mission-based policies, and ensures that keys never co-reside with encrypted data. Edge AI agents use these policies to securely establish PQC-TLS channels between mobile nodes—whether over 5G, satellite, or mesh networks.
Fine-grained control: Access decisions depend on role, location, and mission clearance.
AI automation: Local agents adapt PQC strength and configuration in milliseconds.
Auditability: Every key transaction is PQC-signed and verifiable.
Quantum-ready: Encryption and authentication remain secure against both classical and quantum threats.
Why It Matters
ZAP transforms security from a static, network-based perimeter into a dynamic, data-centric defense layer that anticipates attacks before they happen. Its modular architecture supports not only drones and satellites but also emerging use cases like PQC VPNs for cloud access and secure Open RAN communications.
By combining Zero Trust, AI, and Post-Quantum Cryptography, ZAP represents a proactive, scalable path forward for national security, critical infrastructure, and next-generation mobility ecosystems.
In summary:
Zero Trust AI-Managed PQC isn’t just an academic concept—it’s a roadmap for building resilient, quantum-safe communications that move as intelligently as the systems they protect.